| Oracle® Database 2 Day + Security Guide 11g Release 2 (11.2) Part Number E10575-08 |
|
|
PDF · Mobi · ePub |
| Oracle® Database 2 Day + Security Guide 11g Release 2 (11.2) Part Number E10575-08 |
|
|
PDF · Mobi · ePub |
This chapter contains:
You can configure the client connection to your Oracle Database installation by following the procedures in "Configuring the Network Environment" in Oracle Database 2 Day DBA and the Oracle Database Installation Guide for your platform. This chapter explains how you can encrypt data as it travels through the network, and also provides guidelines that you can follow to secure the network connections for Oracle Database.
This section describes how you can tightens security for the client connection to ensure thorough protection. Encrypting network traffic is essential for securing communications with the database.
These guidelines are as follows:
Because authenticating client computers is problematic, typically, user authentication is performed instead. This approach avoids client system issues that include falsified IP addresses, compromised operating systems or applications, and falsified or stolen client system identities. Nevertheless, the following guidelines improve the security of client connections:
Enforce access controls effectively and authenticate clients stringently.
By default, Oracle allows operating system-authenticated logins only over secure connections, which precludes using Oracle Net and a shared server configuration. This default restriction prevents a remote user from impersonating another operating system user over a network connection.
Setting the initialization parameter REMOTE_OS_AUTHENT to TRUE forces the database to accept the client, operating-system user name received over a nonsecure connection and use it for account access. (To modify an initialization parameter, see "Modifying the Value of an Initialization Parameter".) Because clients, such as PCs, are not trusted to perform operating system authentication properly, it is poor security practice to use this feature.
The default setting, REMOTE_OS_AUTHENT = FALSE, creates a more secure configuration that enforces proper, server-based authentication of users connecting to an Oracle database.
Setting this parameter to FALSE does not mean that users cannot connect remotely. It means that the database will not trust that the client has already authenticated, and will apply its standard authentication processes.
Configure the connection to use encryption.
Oracle network encryption makes eavesdropping difficult. To learn how to configure encryption, see Oracle Database Advanced Security Administrator's Guide.
Set up strong authentication.
See Oracle Database Advanced Security Administrator's Guide for more information about using Kerberos and public key infrastructure (PKI).
Protecting the network and its traffic from inappropriate access or modification is the essence of network security. You should consider all paths the data travels, and assess the threats on each path and node. Then, take steps to lessen or eliminate those threats and the consequences of a security breach. In addition, monitor and audit to detect either increased threat levels or penetration attempts.
To manage network connections, you can use Oracle Net Manager. For an introduction to using Oracle Net Manager, see Oracle Database 2 Day DBA. See also Oracle Database Net Services Administrator's Guide.
The following practices improve network security:
Monitor listener activity.
You can monitor listener activity by using Oracle Enterprise Manager Database Control. In the Database Control home page, under General, click the link for your listener. The Listener page appears. This page provides detailed information, such as the category of alert generated, alert messages, when the alert was triggered, and so on. This page provides other information, such as performance statistics for the listener.
Prevent online administration by requiring the administrator to have the write privilege on the listener password and on the listener.ora file on the server:
Add or modify this line in the listener.ora file:
ADMIN_RESTRICTIONS_LISTENER=ON
Use RELOAD to reload the configuration.
Use SSL when administering the listener by making the TCPS protocol the first entry in the address list, as follows:
LISTENER=
(DESCRIPTION=
(ADDRESS_LIST=
(ADDRESS=
(PROTOCOL=tcps)
(HOST = shobeen.us.example.com)
(PORT = 8281)))
To administer the listener remotely, define the listener in the listener.ora file on the client computer. For example, to access listener USER281 remotely, use the following configuration:
user281 =
(DESCRIPTION =
(ADDRESS =
(PROTOCOL = tcps)
(HOST = shobeen.us.example.com)
(PORT = 8281))
)
)
For more information about the parameters in listener.ora, see Oracle Database Net Services Reference.
Do not set the listener password.
Ensure that the password has not been set in the listener.ora file. The local operating system authentication will secure the listener administration. The remote listener administration is disabled when the password has not been set. This prevents brute force attacks of the listener password.
Remember that the listener password has been deprecated in this release, and will not be supported in the next release of Oracle Database.
When a host has multiple IP addresses associated with multiple NIC cards, configure the listener to the specific IP address.
This enables the listener to monitor all the IP addresses. You can restrict the listener to monitor a specific IP address. Oracle recommends that you specify the specific IP addresses on these types of computers, rather than enabling the listener to monitor all IP addresses. Restricting the listener to specific IP addresses helps to prevent an intruder from stealing a TCP end point from the listener process.
Restrict the privileges of the listener, so that it cannot read or write files in the database or the Oracle server address space.
This restriction prevents external procedure agents spawned by the listener (or procedures executed by an agent) from inheriting the ability to perform read or write operations. The owner of this separate listener process should not be the owner that installed Oracle Database or executes the Oracle Database instance (such as ORACLE, the default owner).
For more information about configuring external procedures in the listener, see Oracle Database Net Services Administrator's Guide.
Use encryption to secure the data in flight.
See "Protecting Data on the Network by Using Network Encryption" to learn about how to protect Oracle data over the network. Oracle Database Advanced Security Administrator's Guide describes network encryption in detail.
Appropriately placed and configured firewalls can prevent outside access to your databases.
Keep the database server behind a firewall. Oracle Database network infrastructure, Oracle Net (formerly known as Net8 and SQL*Net), provides support for a variety of firewalls from various vendors. Supported proxy-enabled firewalls include Gauntlet from Network Associates and Raptor from Axent. Supported packet-filtering firewalls include PIX Firewall from Cisco, and supported stateful inspection firewalls (more sophisticated packet-filtered firewalls) include Firewall-1 from CheckPoint.
Ensure that the firewall is placed outside the network to be protected.
Configure the firewall to accept only those protocols, applications, or client/server sources that you know are safe.
Use a product such as Oracle Connection Manager to multiplex multiple-client, network sessions through a single network connection to the database. It can filter using the source, destination, and host name. This product enables you to ensure that connections are accepted only from physically secure terminals or from application Web servers with known IP addresses. (Filtering using the IP address alone is not enough for authentication, because it can be falsified.)
Prevent unauthorized administration of the Oracle listener.
For more information about the listener, see Oracle Database Net Services Administrator's Guide.
Use the Oracle Net valid node checking security feature to allow or deny access to Oracle server processes from network clients with specified IP addresses. To use this feature, set the following sqlnet.ora configuration file parameters:
tcp.validnode_checking = YES
tcp.excluded_nodes = {list of IP addresses}
tcp.invited_nodes = {list of IP addresses}
The tcp.validnode_checking parameter enables the feature. The tcp.excluded_nodes and tcp.invited_nodes parameters deny and enable specific client IP addresses from making connections to the Oracle listener. This helps to prevent potential Denial of Service attacks.
You can use Oracle Net Manager to configure these parameters. See Oracle Database Net Services Administrator's Guide for more information.
If possible, use Oracle Advanced Security to encrypt network traffic among clients, databases, and application servers. For an introduction to Oracle network encryption, see "Protecting Data on the Network by Using Network Encryption". For detailed information about network encryption, see Oracle Database Advanced Security Administrator's Guide.
Secure the host operating system (the system on which Oracle Database resides).
Secure the host operating system by disabling all unnecessary operating system services. Both UNIX and Windows platforms provide a variety of operating system services, most of which are not necessary for typical deployments. These services include FTP, TFTP, TELNET, and so forth. Be sure to close both the UDP and TCP ports for each service that is being disabled. Disabling one type of port and not the other does not make the operating system more secure.
In addition to protecting information by encrypting it at the database level, you must protect it as it travels across the network.
This section contains:
See Also:
Oracle Database Advanced Security Administrator's Guide for detailed information about network encryptionNetwork encryption refers to encrypting data as it travels across the network between the client and server. The reason you should encrypt data at the network level, and not just the database level, is because data can be exposed on the network level. For example, an intruder can use a network packet sniffer to capture information as it travels on the network, and then spool it to a file for malicious use. Encrypting data on the network prevents this sort of activity.
To encrypt data on the network, you need the following components:
An encryption seed. The encryption seed is a random string of up to 256 characters. It generates the cryptographic keys that encrypts data as it travels across the network.
An encryption algorithm. You can specify any of the supported algorithm types: AES, RC4, DES, or 3DES.
Whether the settings apply to a client or server. You must configure the server and each client to which it connects.
How the client or server should processes the encrypted data. The settings you select (you have four options) must complement both server and client.
A mechanism for configuring the encryption. You can use Oracle Net Manager to configure the encryption. Alternatively, you can edit the sqlnet.ora configuration file. Both Oracle Net Manager and the sqlnet.ora file are available in a default Oracle Database installation.
You can configure network encryption by using either Oracle Net Manager or by editing the sqlnet.ora file. This guide explains how to use Oracle Net Manager to configure network encryption.
To configure network encryption:
On the server computer, start Oracle Net Manager.
UNIX: From $ORACLE_HOME/bin, enter the following at the command line:
netmgr
Windows: From the Start menu, click All Programs. Then, click Oracle - HOME_NAME, Configuration and Migration Tools, and then Net Manager
From the Oracle Net Configuration navigation tree, expand Local, and then select Profile.
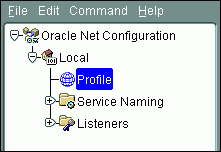
From the list, select Oracle Advanced Security.
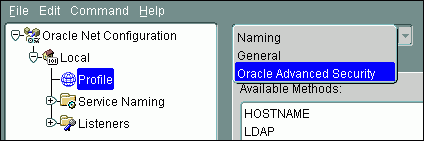
Under Oracle Advanced Security, select the Encryption tab.
The Encryption settings pane appears.
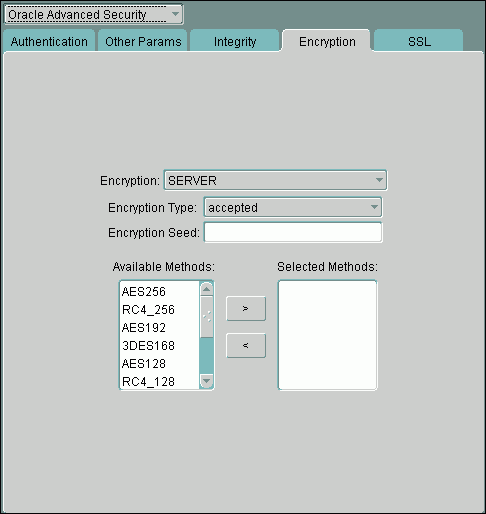
Encryption: From the list, select SERVER to configure the network encryption for the server. (For the client computer, you select CLIENT.)
Encryption Type: Select from the following values to specify the actions of the server (or client) when negotiating encryption and integrity:
accepted: Service will be active if the other side of the connection specifies either required or requested, and there is a compatible algorithm available on the receiving database; it will otherwise be inactive.
rejected: Service must not be active, and the connection will fail if the other side requires any of the methods in this list.
requested: Service will be active if the other side of the connection specifies either accepted, required, or requested, and there is a compatible algorithm available on the other side. Otherwise, the service is inactive.
required: Service must be active, and the connection will fail if the other side specifies rejected, or if there is no compatible algorithm on the other side.
Encryption Seed: Enter a random string of up to 256 characters. Oracle Database uses the encryption seed to generate cryptographic keys. This is required when either encryption or integrity is enabled.
If you choose to use special characters such as a comma [,] or a right parenthesis [)] as a part of the Encryption Seed parameter, enclose the value within single quotation marks.
Available Methods: Select one or more of the following algorithms, and use the move button (>) to move them to the Selected Methods list. The order in which they appear in the Selected Methods list determines the preferred order for negotiation. That is, the first algorithm listed is selected first, and so on.
AES256: Advanced Encryption Standard (AES). AES was approved by the National Institute of Standards and Technology (NIST) to replace Data Encryption Standard (DES). AES256 enables you to encrypt a block size of 256 bits.
RC4_256: Rivest Cipher 4 (RC4), which is the most commonly used stream cipher that protects protocols such as Secure Sockets Layer (SSL). RC4_256 enables you to encrypt up to 256 bits of data.
AES192: Enables you to use AES to encrypt a block size of 192 bits.
3DES168: Triple Data Encryption Standard (TDES) with a three-key option. 3DES168 enables you to encrypt up to 168 bits of data.
AES128: Enables you to use AES to encrypt a block size of 128 bits.
RC4_128: Enables you to use RC4 to encrypt up to 128 bits of data.
3DES112: Enables you to use Triple DES with a two-key (112 bit) option.
DES: Data Encryption Standard (DES) 56-bit key. Note that National Institute of Standards and Technology (NIST) no longer recommends DES.
RC4_40: Enables you to use RC4 to encrypt up to 40 bits of data. (Not recommended.)
DES40: Enables you to use DES to encrypt up to 40 bits of data. (Not recommended.)
From the File menu, select Save Network Configuration, and then select Exit to exit Oracle Net Manager.
Repeat these steps for each client computer that connects to the server.
See Also:
Oracle Database Net Services Reference for information about editing the sqlnet.ora file parameters to configure network encryption
Oracle Database Advanced Security Administrator's Guide for more information about network data encryption
Table 5-1 lists initialization parameters that you can set to better secure user accounts.
Table 5-1 Initialization Parameters Used for Network Security
| Initialization Parameter | Default Setting | Description |
|---|---|---|
|
|
Specifies a prefix that Oracle Database uses to identify users attempting to connect to the database. Oracle Database concatenates the value of this parameter to the beginning of the user operating system account name and password. When a user attempts a connection request, Oracle Database compares the prefixed username with user names in the database. |
|
|
No default setting |
Specifies a network name that resolves to an address or address list of Oracle Net remote listeners (that is, listeners that are not running on the same computer as this instance). The address or address list is specified in the |
|
|
|
Specifies whether remote clients will be authenticated with the value of the |
|
|
|
Specifies whether operating system roles are allowed for remote clients. The default value, |
To modify an initialization parameter, see "Modifying the Value of an Initialization Parameter". For detailed information about initialization parameters, see Oracle Database Reference andOracle Database Administrator's Guide.